This is an old revision of the document!
Table of Contents
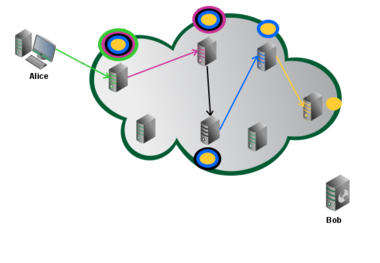
Tox over Tor
With the ever increasing need for anonymity online, Toxcore now supports TCP-only communications to be used through services such as Tor. Tunneling Tox over Tor allows the user to still communicate with non-Tor contacts, unlike I2P, providing the best of both worlds. The following guide will explain how to setup ToT with the various Tox clients.
Installing Tor
Tor must be installed prior to tunneling Tox. To keep resource usage low, we recommend installing just Tor itself, and avoiding the use of the Tor Browser Bundle. You may use the TBB if you wish, but the following directions are how to install Tor itself as a tunnel only.
Debian, Ubuntu, Knoppix, etc.
- Install Tor by running sudo apt-get install tor.
- Start Tor by running sudo service tor start.
Fedora, CentOS, RHEL, etc.
- Paste the following into
/etc/yum.repos.d/torproject.repo:[tor] name=Tor repo enabled=1 baseurl=http://deb.torproject.org/torproject.org/rpm/DISTRIBUTION/$basearch/ gpgcheck=1 gpgkey=http://deb.torproject.org/torproject.org/rpm/RPM-GPG-KEY-torproject.org.asc [tor-source] name=Tor source repo enabled=1 autorefresh=0 baseurl=http://deb.torproject.org/torproject.org/rpm/DISTRIBUTION/SRPMS gpgcheck=1 gpgkey=http://deb.torproject.org/torproject.org/rpm/RPM-GPG-KEY-torproject.org.asc
- Confirm the GPG repo key:
3B9E EEB9 7B1E 827B CF0A 0D96 8AF5 653C 5AC0 01F1 - Run
sudo yum install torto install Tor - Start Tor by running
sudo service tor start
Windows
Download the Tor Expert Bundle and install, located here.
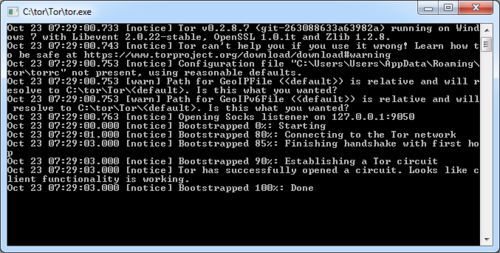
When you run Tor, you should see a window similar to the one shown on the right.
Take note of the line saying
Opening Socks listener on Address:Port
Android
Orbot required. Available on F-Droid.
Tunneling
Clients
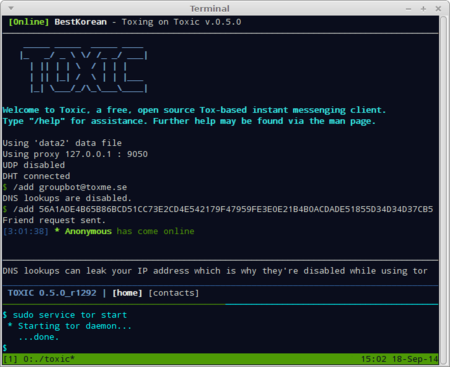
Toxic
- Verify Tor is running
- Run
toxic –force-tcp –SOCKS5-proxy 127.0.0.1 9050
qTox
- Verify Tor is running.
- Launch qTox, and navigate to settings by clicking on the cogwheel in the lower left-hand corner.
- Look under the General tab in settings and scroll down to the bottom to, Connection Settings.
- Uncheck UDP option to set it off.
- Uncheck IPv6 option to set it off.
- Set the Proxy type to SOCKS5.
- Address to 127.0.0.1 and Port 9050 (Port 9150 if you use Tor Browser).
- If you don't connect to the Tox network immediately, restart qTox and it should automatically connect to the Tox network via Tor.
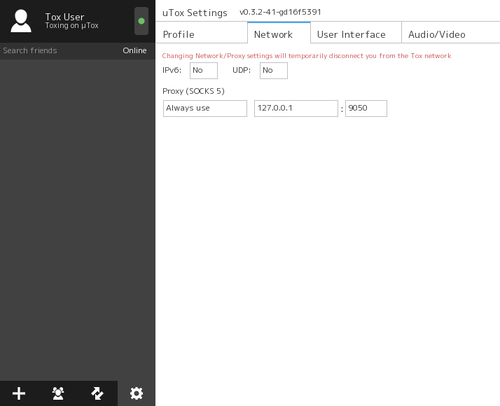
µTox
- Verify Tor is running
- Launch uTox, and navigate to settings by clicking on the cogwheel in the lower left-hand corner
- Switch to the Network tab
- Set the IPv6 option to no
- Set the UDP option to no
- Set the Proxy to “Always Use”, and input the value 127.0.0.1 for the IP and 9050 for the port (9150 if you use Tor Browser).
- If you don't connect to the Tox network immediately, restart uTox and it should automatically connect to the Tox network via Tor.
TRIfA
- Make sure Orbot is installed and started first.
- Launch TRIfA, and navigate to Settings by clicking on the three lines in the upper left-hand corner
- In General, move the slider of
enable Tor proxyto enabled position. - Shut down the TRIfA client and start it again.